Qt X System security
Qt X devices can be secured from either the Qt X software or web UI. Securing a device allows for protection from any attacks including denial of service, intentional misconfiguration, and theft of credentials if deployed on a network that is not firewalled or adequately protected
Qt X devices are shipped in an 'unprotected' state to allow installers to configure and use the device without explicit authentication or authorization. Protected devices and systems will require authentication and authorization which may be provided explicitly by the user or implicitly via an approved client application such as SageVue.
The methods and user roles available when protecting a Qt X system are outlined below for both Qt X software and web UI configuration.
System security via Qt X application
Password-protect a system via the Security button on the Devices & Systems window. A system must be selected from the list for the security button to be available:
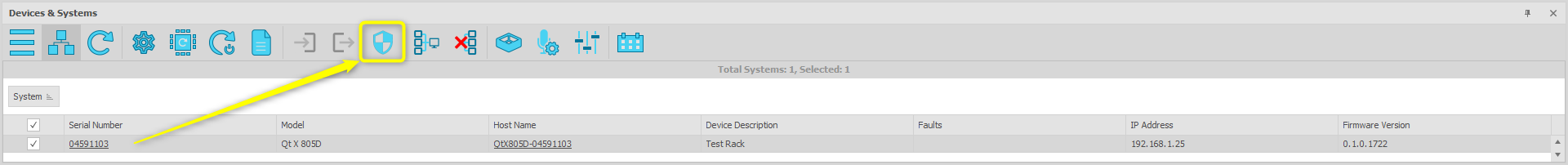
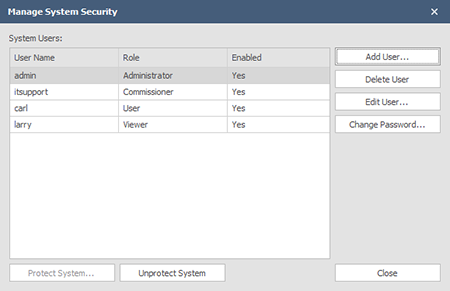
To protect a system click the Security button as shown above. The Manage System Security dialog will appear on an un-protected system:
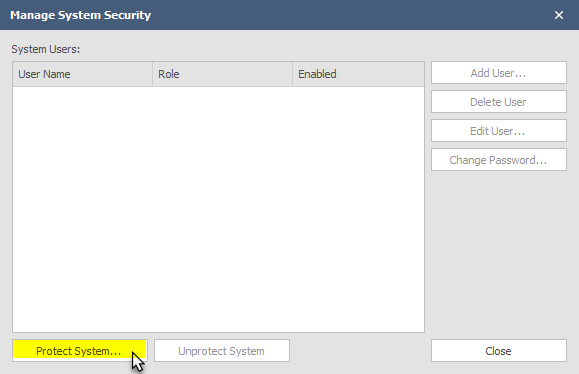
Click Protect System to add security settings. When a system is protected for the first time the user must set up an Admin account. This account will have rights to all settings, including creating users, deleting users, and setting a user's level of access:
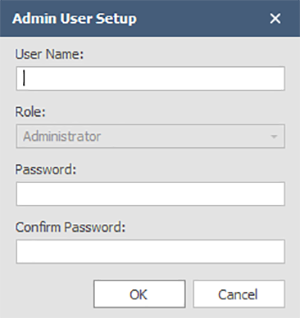
The user name must be alphanumeric without spaces. The password must be between 8 and 64 characters. Once an admin account has been created, other user roles may be assigned:
The System Security window will reflect the System Users and their respective roles once they have been created:
For detailed descriptions of user roles, see the tables located here.
System security via web UI
Use the system settings tab to access systems security in the web UI.
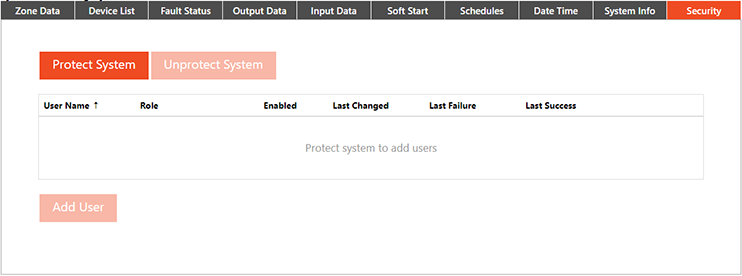
Set the Admin security level. The user name must be alphanumeric without spaces. The password must be between 8 and 64 characters. Enter the information and press save.
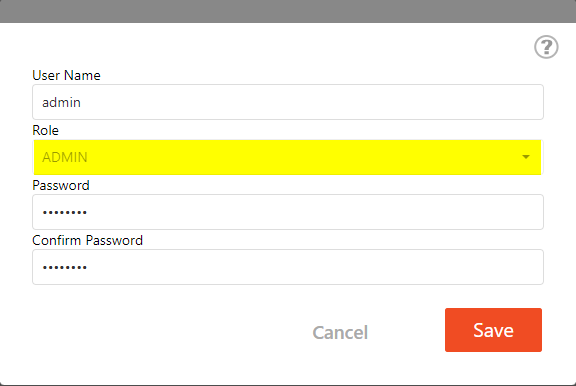
IMPORTANT: Document the admin user name and password. If lost, it is unrecoverable.
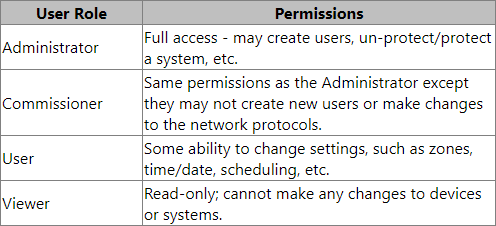
Once an Admin security level is set additional security levels may be set. The table below gives a high-level overview of the types of permissions that each user role has.

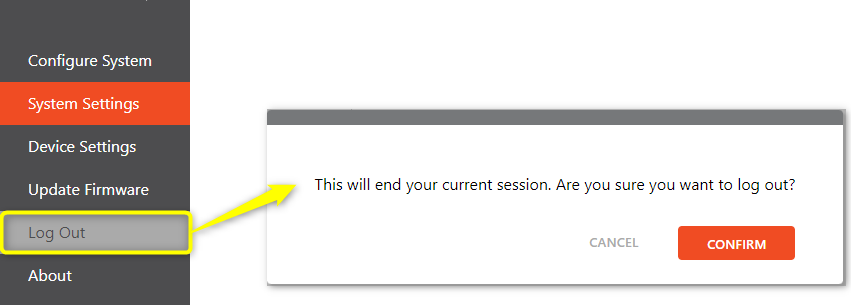
Note: Once the system is protected the side menu will reflect a logout tab. Clicking on Logout will bring up an additional screen asking to confirm. Once Confirm is pressed you will be logged out of the system
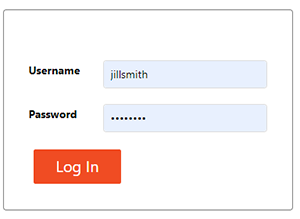
If the user has logged out of the system, a login screen will appear when the system is accessed by the Web UI. A Username and corresponding password must be entered to access the system controls.

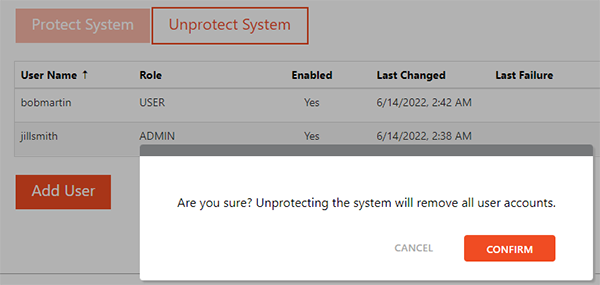
Unprotecting system
An Admin-level user may also Unprotect the system. Once unprotected all user information will be deleted.