Audia-Nexia Performing a Wireshark trace of a Biamp VoIP device
This document describes the process of performing a packet capture of Biamp VoIP device communications on a VoIP network. A program called Wireshark is a free, open-source packet analyzer that is used for network troubleshooting and analysis.
If a Biamp VoIP device is on the VoIP network but not registering with the Proxy Server determining the point of failure can be difficult using the Biamp software alone. The registration process may be hindered by something beyond the VoIP card itself. Possible causes can include communications issues over the network or issues with the configuration of the Proxy Server. If this is the case, Wireshark can be used to help locate the point of failure.
Get Wireshark
Go to the Wireshark download page at http://www.wireshark.org/download.html
Download the Wireshark installer and install Wireshark.
Mirror a port
To perform a Wireshark capture of the VoIP packet flow the computer running the Wireshark program must be able to see all information going to and from the Biamp VoIP device. One way to do this is by configuring a mirrored port on a network switch, which essentially tells the switch to copy all of the traffic going to/from the VoIP device and send it to the PC. There are three different methods used to mirror the VoIP network communications:
Method 1 - Via a Managed Switch
- The Biamp VoIP device will be connected to the VoIP Network using an Ethernet Switch. Typically the switches used in this setting will be managed switches and the functionality of the ports can be manipulated. If this is the case, contact an IT Administrator who is able to change the port settings of this switch and ask to be provided with a mirrored port of the Biamp VoIP port. Mirroring a port is a common method of monitoring of network traffic and is used on a managed switch to send a copy of packets seen on one switch port to a network monitoring connection on another switch port.
- Once port mirroring has been set up proceed to "Capture a Wireshark Trace".
Method 2 - Using a secondary Managed Switch
- If it is not possible to gain access to the main network switch of the VoIP system a secondary managed Ethernet switch can be used to monitor the network traffic to and from the Biamp VoIP device. The secondary switch in this case must have the ability to provide port mirroring.
- Setup the port mirroring in the managed switch. Every switch setup is a bit different and specific issues with setting up the mirrored port should be directed to the switch manufacturer.
- Connect the computer running Wireshark to the destination port of the managed switch. The destination port is defined as the port to which traffic is mirrored.
- Connect the Biamp VoIP device to the source port of the managed switch. The source port is defined as the port from which traffic is mirrored.
- Connect a feed from the main VoIP Ethernet switch to the Ethernet switch being used for the port mirroring.
- Proceed to "Capture a Wireshark Trace".
Method 3 - Through a network tap
- If a managed switch is not available it is possible to use a network tap to perform the Wireshark capture. A network tap captures bi-directional network traffic and mirrors it to a designated tap port. It should be placed between the Ethernet network switch and the Biamp VoIP port. The tap should support 10/100Base-T links at a minimum.
- Connect a feed from the main VoIP Ethernet switch to the Ethernet tap.
- Connect the Biamp VoIP device to the mirrored port of Ethernet tap.
- Connect the computer running Wireshark to the mirroring port of the Ethernet tap.
- Proceed to "Capture a Wireshark Trace".
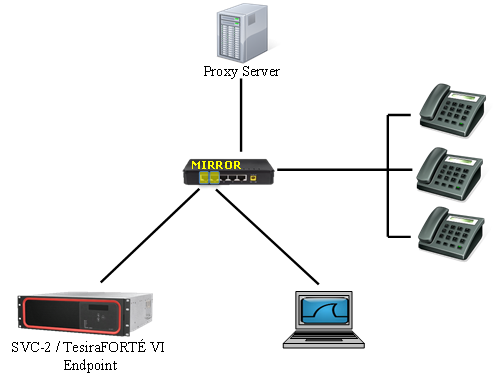
Topology
The three methods of performing a Wireshark trace use slight variations on the following topology.
Capture a Wireshark trace
- Open Wireshark.
- In the Capture pull down menu select Options.
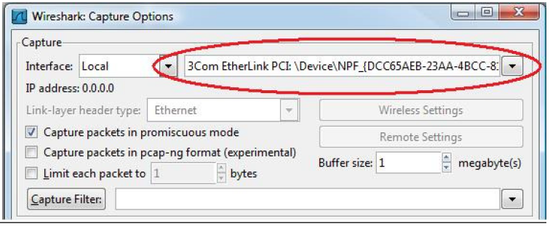
- Select the Network Interface Card of your computer that Wireshark should use to perform the capture.
Figure 1 – Select a NIC
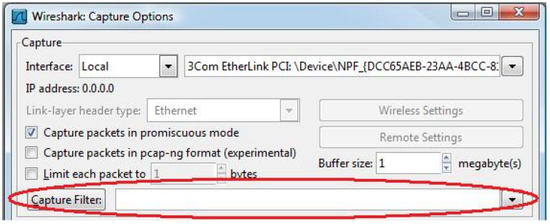
- Ensure that the Capture Filter field is blank. Filtering the capture may exclude packets that are needed to solve the problem from the Wireshark trace.
Figure 2 – Clearing the Capture Filter
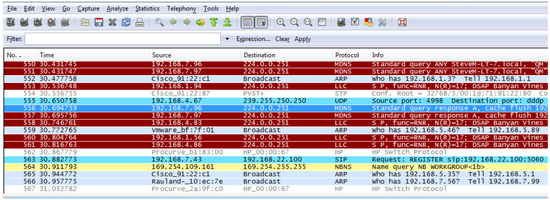
- Select Start on the bottom of the Capture Options Window to start the Wireshark Capture. You should now see a scrolling list of packets being displayed in the Wireshark window. If this list does not appear there may be a problem with the port mirroring process described previously in this document.
Figure 3 – Scrolling List of a Wireshark Trace
- With the Wireshark capture running, unplug the Biamp VoIP device from the switch for 5 seconds then plug back in. This will cause the VoIP device to start its registration over again while Wireshark documents the process.
- Depending on the specific nature of the problem it may be necessary to make a call to or from the VoIP device with Wireshark running in order to further troubleshoot.
- When all captures have been completed stop the current trace by selecting Stop from the Capture pull down menu.
Verifying the correct data was captured
To confirm the correct data has been captured use the Wireshark filter field. By entering the word ‘sip’ (in lowercase), the SIP negotiation sequence between the Biamp VoIP device and the Proxy can be seen. Note that if no SIP messages are shown, the Wireshark capture has not been performed correctly and will need to be retaken using the correct settings. The most common reason for this is the port mirror being incorrectly configured.
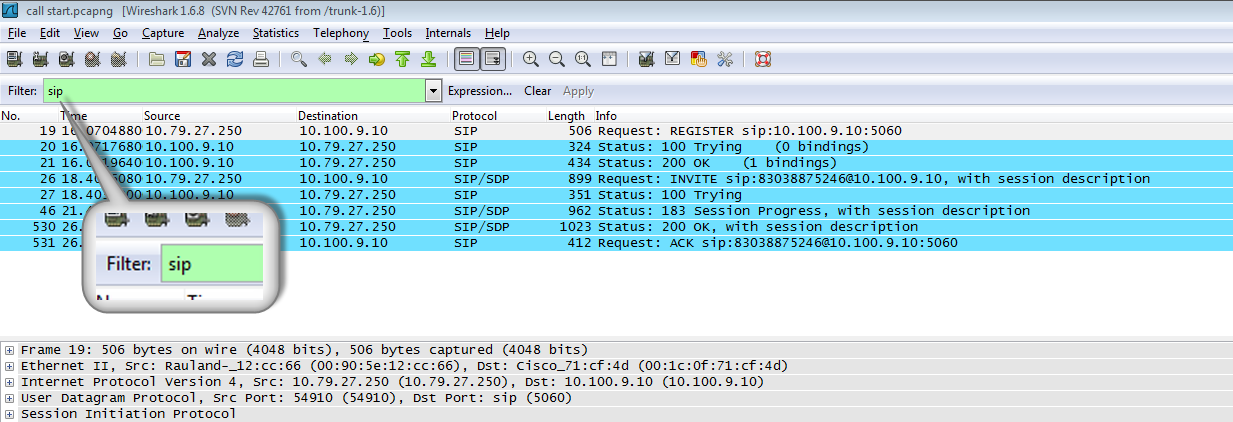
- Choose File-->Save As to save a copy of the Wireshark capture to the computer.
- Proceed to the How to read a Wireshark trace of a Biamp VoIP device article to continue troubleshooting the system.
Privacy concerns
|
IMPORTANT - A Wireshark trace captures (or records) all of the packets sent to and from a VoIP endpoint. This means that it is possible to listen to the calls which have been captured from the Wireshark data. This can be an important part of troubleshooting for VoIP systems which are malfunctioning. You should not perform a Wireshark trace on client systems during sensitive calls as you will be recording the call, which can be a violation of many wiretapping laws if the participants are unaware of the recording being made. If you are troubleshooting cases where calls fail only intermittently and you need to take a long duration capture of all traffic for a VoIP card be sure to impress upon your clients that the calls are being recorded during that time period. You may need to provide clear notification to both parties on a call that captures are being made. Additionally, there may be a need to have signed Non-Disclosure Agreements for such cases. Be sure to discuss this with the client before making captures of their calls. Captures made of calls which do not contain private conversations, with full disclosure of the process, and specifically for troubleshooting problematic VoIP issues should not be a problem. |