Control Tunneling
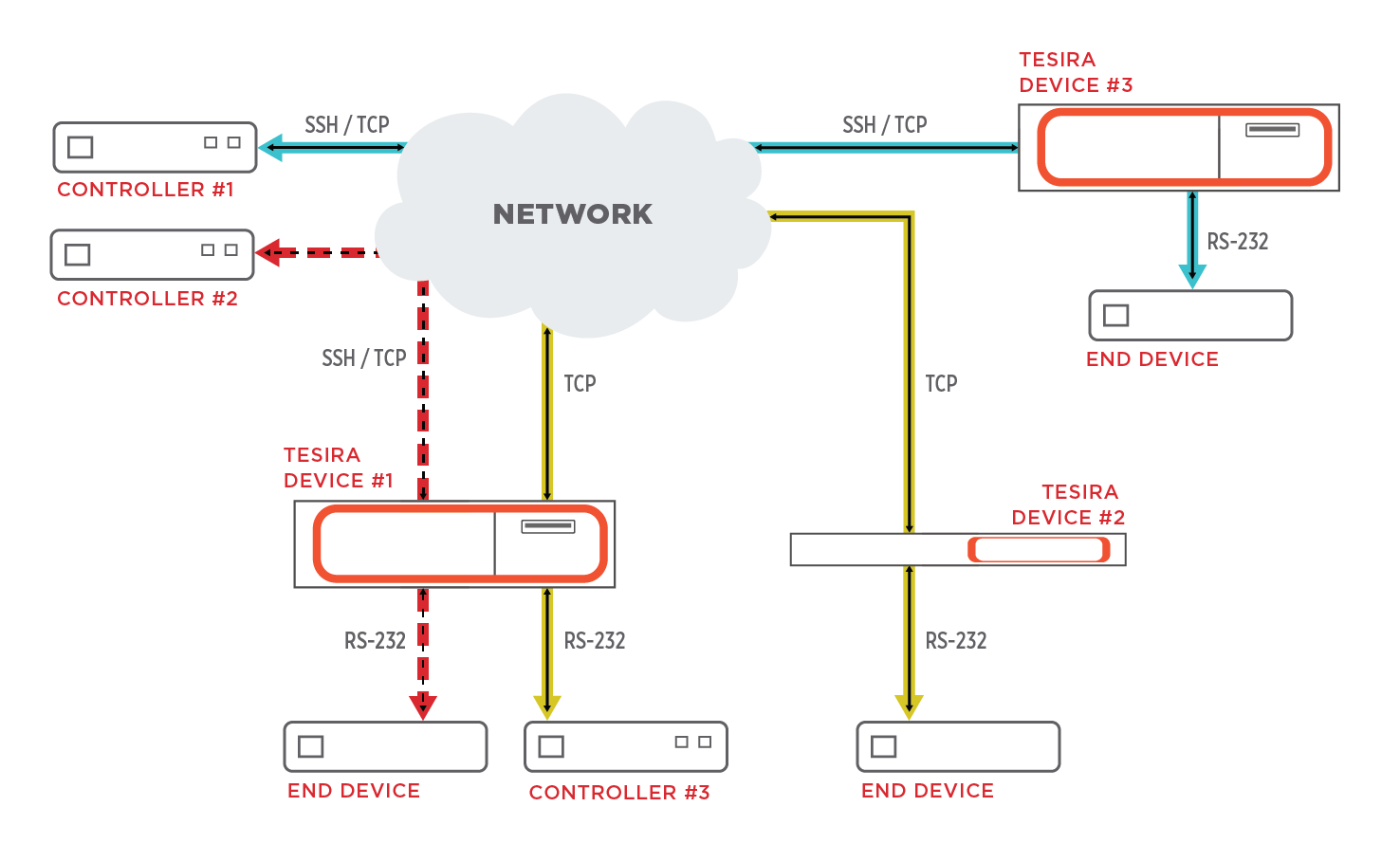
The Control Tunneling feature allows bi-directional communication tunnels to be created in a Tesira system. Each Control Tunnel is point-to-point within a single Tesira system and can be configured as Serial-to-Serial or SSH-to-Serial. Once the Control Tunnels have been established, third-party control products may use them to control connected devices such as displays or Pan-Tilt-Zoom (PTZ) cameras.
Control Tunneling is supported on TesiraFORTE, TesiraLUX, SERVER-IO and SERVER devices that are running Tesira firmware version 3.8 or later. However, it is not currently supported on redundant SERVER pairs or EX-LOGIC expanders.
Control Tunnel types
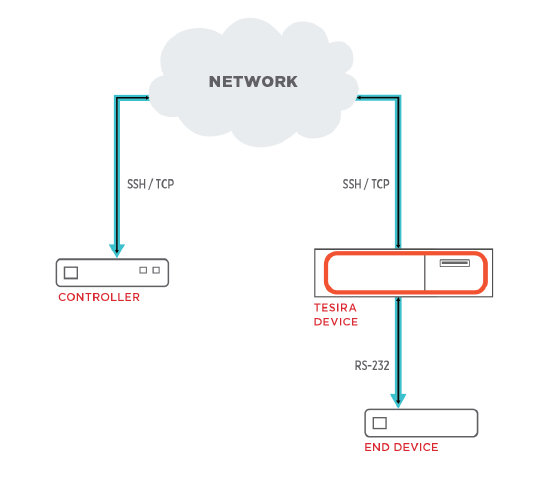
SSH-To-Serial Tunnel
The SSH-to-Serial Tunnel allows a third-party controller to establish an SSH session with a Tesira server class device (within a Tesira system) and communicate via its serial port. Once configured, this SSH Control Tunnel acts like a serial port extender using SSH. The third-party controller authenticates with the Tesira device to send and receive serial commands via the connect RS-232 port. An example is shown below:
Creating and editing Control Tunnels
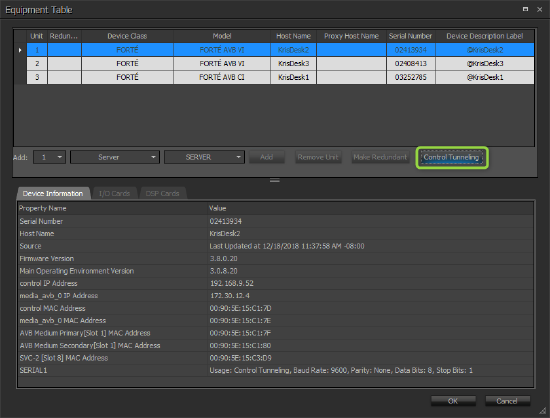
The initial creation of a Control Tunneling requires two distinct steps. The first step involves defining the 1:1 tunnel map as part of the Equipment Table. The second step involves configuring the device serial port settings in Device Maintenance.
1) Define the Control Tunnel map
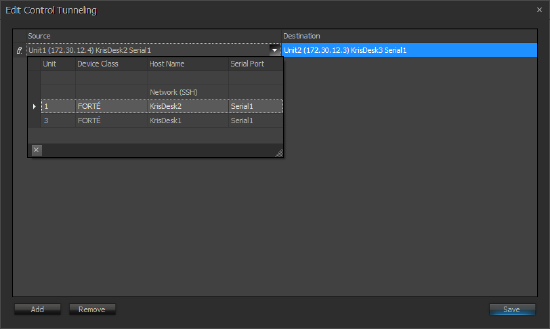
- Select the Source:
- Network (SSH)
- Serial port of a Tesira device in the Equipment List
- Select the Destination.
- Select the appropriate serial port of the Tesira device connected to the device being controlled.
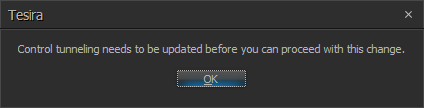
The Control Tunnel is a one-to-one assignment within a Tesira system. If changes are made to the equipment table that affects existing Control Tunnels, Tesira software will notify the user with the following error:
The Control Tunnel map must be corrected or updated before the Equipment Table changes can take place.
Control Tunnels are established when the Tesira configuration is sent to the Tesira hardware.
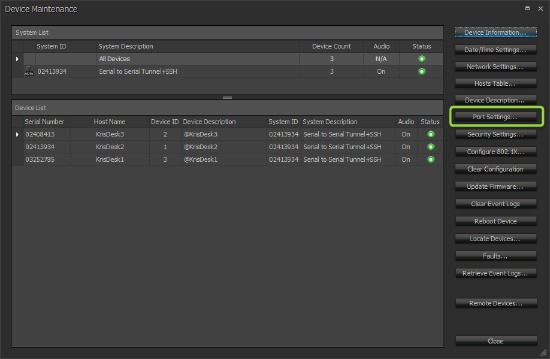
2) Configure device serial port settings
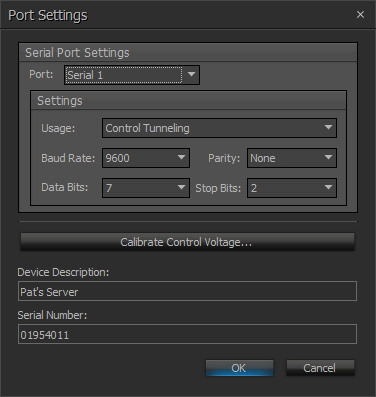
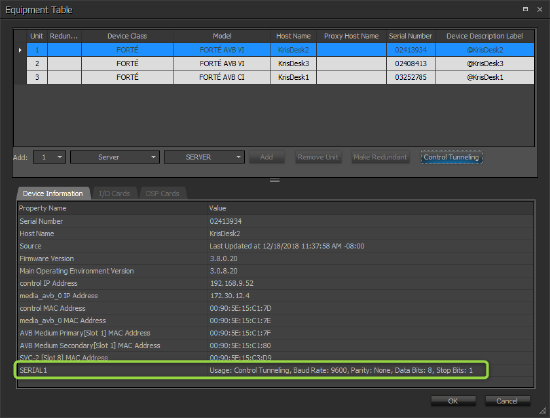
The Tesira Serial ports included in a Control Tunnel must be configured to match the Usage and Baud Rate needs of the connected controlled device or controller. These configuration changes are made in the Port Settings section of Device Maintenance for each respective Tesira device.
- The Tesira device must be rebooted to apply the changes.
When these steps have been completed, the Equipment Table will confirm serial port settings:
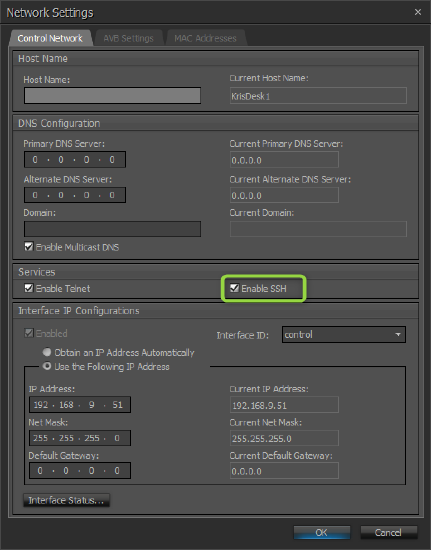
3) Enable SSH
If an SSH-To-Serial Tunnel is defined, SSH must be enabled on that Tesira device via Device Maintenance > Network Settings.
4) Authenticate
Each SSH-To-Serial Tunnel supports one active user session at a time. The third-party controller must create an SSH session directly with the Tesira device that is hosting the SSH-to-Serial Control Tunnel, and will be required to authenticate using the following credentials:
- Serial port 1:
- Username: serial_control_1
- Password: (none)
- Serial port 2 (only available on Tesira Server and Server-IO):
- Username: serial_control_2
- Password: (none)
Troubleshooting
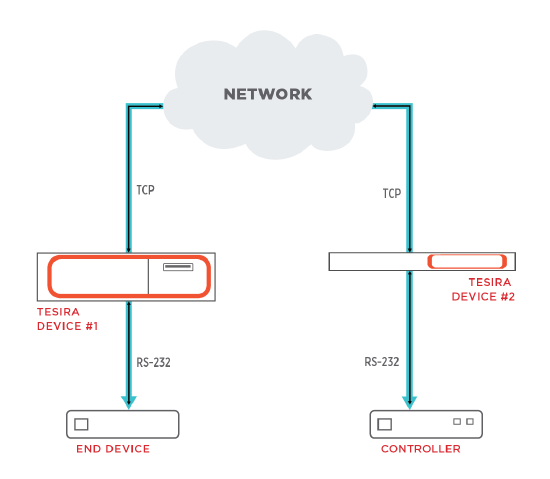
Serial-To-Serial Tunnel
- Tesira devices are DCE devices with female DE-9 connections. Pin 2 is TxD and Pin 3 is RxD. A Serial-To-Serial Tunnel being DCE at both ends will essentially behave like a crossover cable. In some cases, a null modem adapter may be required for proper Tx/Rx pin alignment.
- A USB-to-Serial adapter can be used to manually send/receive strings to/from the configured Tesira Control Tunnel using a terminal emulator such as PuTTY. This will allow a computer to act as the controller or the controlled device and confirm traffic traversal.
- The Serial-to-Serial Tunnel establishes a TCP session between the Tesira devices. This means Wireshark can be used to capture the clear text strings traversing that Control Tunnel.
- If changes are made to the Tesira Serial Port, be sure to reboot the device to implement these changes.
- If the Tesira device receives a significant change (IP change, device configuration, serial port change, reboot, etc.), associated existing control tunnels will be suspended, and faults will be reported until the tunnels automatically reconnect.
- Tesira Event Logs include information regarding Control Tunnel status. Log entries will be captured if a tunnel is cleared, created or has a fault state. This information can be used for troubleshooting.
SSH-To-Serial Tunnel
- Confirm that SSH is enabled on the Tesira device (Device Maint. > Network Settings).
- If changes are made to the Tesira Serial Port, be sure to reboot the device to implement these changes.
- A USB-to-Serial adapter can be used to manually send/receive strings to/from the configured Tesira Control Tunnel using a terminal emulator such as PuTTY. This will allow a computer to act as the controlled device and confirm traffic traversal.
- PuTTY also allows a PC to establish an SSH session with the Tesira device configured for SSH-To-Serial Tunneling. Device-specific test commands can be used to troubleshoot.
- The SSH-To-Serial Tunnel supports only one active SSH client session. If a subsequent client attempts to authenticate, the "Too many logins..." response will be received and the connection refused. PuTTY may simply close the session (unless logging is enabled to see the message in the log file).
- If the Tesira device receives a significant change (IP change, device configuration, serial port change, reboot, etc.), associated existing control tunnels will be suspended. The control system SSH clients will need to re-authenticate once the changes are complete.
- When using hexadecimal commands to control a device, confirm the strings being sent from the controller match the strings arriving at the Tesira serial port. The Tesira SSH-To-Serial Tunnel passes the data in a raw format to the serial port. Some SSH modules may use a unicode conversion that modifies the original hex commands rendering them non-functional. If you reach this conclusion, please contact Support@biamp.com for further assistance.
- Tesira Event Logs include information regarding Control Tunnel status. Log entries will be captured if a tunnel is cleared, created or has a fault state. This information can be used for troubleshooting.
- There have been field reports of IGMP Proxy on Control Subnet of Crestron processors causing tunnel stability issues. It is recommended to disable IGMP Proxy for improved stability.