Tesira security best practices
Security is an important consideration in many AV installations. In high security environments, it's critical to install Tesira devices according to best practices. This article describes best practices for securely deploying Tesira equipment to minimize the risk of unauthorized access to a Tesira system. See Network Security for an overview of security terminology and practices.
Prerequisites and assumptions
The following prerequisites and assumptions are made for securely deploying a Tesira system:
- The technician configuring Tesira security has completed TesiraFORTE Online Training at a minimum and understands device maintenance functions.
- Physical access to devices is secured. Unauthorized physical access may result in tampering or factory reset.
- Network equipment is secured following switch vendor recommended best practices.
- The latest firmware and software versions of Tesira are installed.
- A patch management plan includes regular Tesira firmware updates.
Network interfaces
This section provides an overview of the networking functionality of Tesira devices. Tesira SERVER, SERVER-IO and TesiraFORTE server-class models are optionally configurable with a variety of network interfaces:
| Network Port Function | 802.1X Support | Stream Encryption |
|---|---|---|
| Tesira Control | Yes | N/A |
| VoIP | Yes | Yes |
| AVB Media | Yes | No |
| CobraNet Media | No | No |
| Dante Media | No | No |
Network isolation provides the greatest level of security. However, it may limit functionality of a system. Care should be taken to isolate networks where the functionality of the AV system design allows. For example, the Tesira control port and Dante media port are not required to connect the same network or VLAN, but certain Dante device control functions, such as microphone mute LED state, are not available if the networks are isolated.
See Tesira network ports and protocols for detailed information regarding the ports active on each interface.
See 802.1X for more detail on implementing network interface access control.
Tesira control port
All Tesira server-class devices have a control port. The Tesira control port provides connectivity with Tesira Software, Biamp Canvas, Biamp SageVue, other Tesira devices within the same system configuration, and Telnet or SSH interfaces for third-party control automation systems. The control port is connected to the AVB interface via the DSP host processor. Network traffic is not routed or switched automatically between interfaces and control functions on the AVB port may be disabled. The control and AVB ports are not connected to any other interfaces.
VoIP Port
The VoIP port is an isolated network interface. It supports TLS, SIPS, and SRTP. Secure protocols rely on compatibly with the VoIP proxy server. Best security practices of the VoIP proxy system should be followed in the Tesira VoIP configuration. Follow the Tesira VoIP configuration guides for the given VoIP proxy system.
AVB media port
The AVB media port uses the IEEE 802.1BA Audio Video Bridging media protocol. This protocol is also used by Tesira audio expander-class devices. The AVB protocol does not encrypt stream traffic. Isolate AVB networks were appropriate. Since AVB is managed within the switch configuration, follow switch vendor recommendations to disable the AVB protocol entirely on unused ports. The switch controls end-point access to the AVB protocol. When the switch port does not have AVB protocols enabled, media end-points are completely denied any stream traffic.
The AVB media port also provides control communications with Tesira control expanders and audio expanders. IP communications are enabled by default on the AVB port and may be disabled. However, Tesira expander devices on the AVB network will lose functionality if IP control is disabled on the AVB media interface.
CobraNet media port
CobraNet is a propriety protocol provided by Cirrus Logic Inc. It is a legacy protocol that doesn't posses any security mechanisms. Best practice is to isolate the CobraNet network. CobraNet is only available on the Tesira SERVER / SERVER-IO models via the SCM-1 card. The card does not provide any connection to other network interfaces on the Tesira device.
Dante media port
Dante is a proprietary protocol provided by Audinate Pty Ltd. and is available on the TesiraFORTE DAN models and server chassis models via the DAN-1 card. The DAN-1 card contains Dante module hardware provided by Audinate. Dante end point access control may be implemented using Dante Domain Controller (DDM). DDM software is obtained from Audinate outside of Biamp. DDM software will encrypt control communications with audio end points. Dante does not encrypt the flow (stream) traffic. See Audinate's page on Dante Domain Manager for more detail.
Tesira device deployment
To reduce the risk of unauthorized access, consider the following strategies while deploying a Tesira server-class device. Discussed further in this article, Biamp SageVue provides centralized mechanisms for managing Tesira system security, protocol state and 802.1X.
Enable Tesira System Security
After the DSP configuration has been sent to the Tesira system, you may next enable System Security. A Tesira system configuration may contain multiple devices and enabling security creates an admin user for all devices in the system. Each Tesira system has its own admin and user accounts. The account is not shared across multiple systems.
Tesira provides the following user privilege levels:
| Privilege Level |
View |
Change | Alter Presets |
Start/Stop Audio |
Edit DSP Layout File |
Device Maintenance |
Modify Users |
|---|---|---|---|---|---|---|---|
| Observer | X | ||||||
| Controller | X | X | |||||
| Supervisor | X | X | X | X | |||
| Designer | X | X | X | X | X | ||
| Administrator | X | X | X | X | X | X | X |
The observer user may only connect to the system and view DSP objects and meters. The controller user may change DSP object settings, such as level controls or mixer crosspoints. The controller privilege level is the minimum required for any control of the system.
Users may change their own passwords later. Only the admin account may modify user accounts and perform device maintenance functions. The only mechanism to recover a lost admin password is to factory reset the device. This will also clear the DSP configuration. This process requires physical access to the back panel of the device.
Caution: Biamp Canvas and TTP (Tesira Text Protocol) will require a username and password when Tesira system security is enabled. A minimum permission level of Controller will be required for any connected third-party control automation systems. Coordinate with the control automation programmer before enabling system security. Any existing control systems won't be functional until they are updated with correct Tesira credentials.
Enabling System Security
- After the DSP has been configured, connect to the unprotected Tesira system with Tesira Software.
- Open the System menu > Security menu > Manage System Security...
- Click the "Protect System..." button to create the admin user. All subsequent user and device maintenance operations with the system will require the admin account. Reconnect to the system when prompted after creating the admin user.
- Add a user with Controller permissions for Biamp Canvas or any connected third-party control automation system.
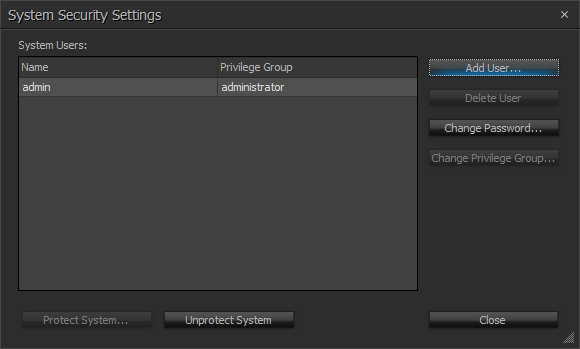
- Create user accounts for any technicians that need to maintain the system.
Disable Telnet and SSH
The Tesira Control port has Telnet and SSH text consoles. They do not facilitate interactive operating system login. Telnet and SSH are disabled by default and may be enabled to support TTP (Tesira Text Protocol) interfaces used by third-party control automation systems. Use SSH or Serial RS-232 interfaces for TTP where possible. The use of Telnet is discouraged.
Disable IP communications on AVB port
Tesira server-class devices by default have Tesira IP control traffic enabled on the AVB ports. IP Communicates are used for inter-device control. This faciliates the "separated networks" and "single network connection" topologies in Tesira. If the AVB network does not have Tesira expander-class devices, such as amps and microphones, or single network connection topology is not in use, disable control communication on the AVB port. AVB streaming between Tesira server-class devices does not require IP communications.
- Open Device Maintenance in Tesira Software
- Open the Network Settings for the Tesira device.
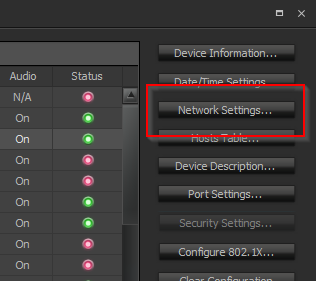
- On the Control tab under Interface IP Communications, select the "media_avb_xx" interface ID.
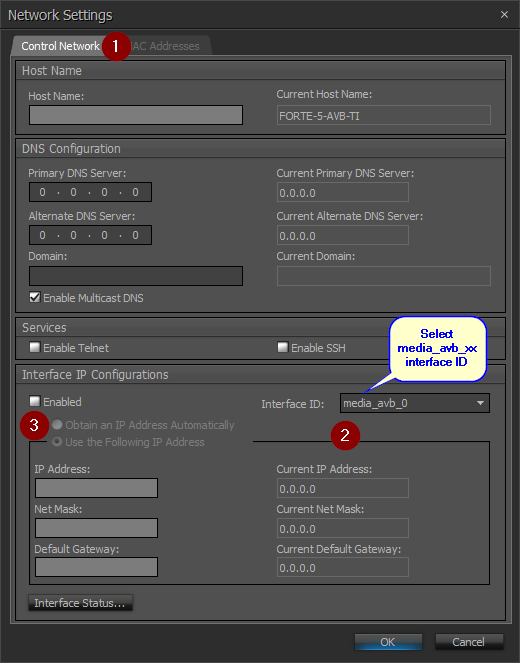
- Uncheck the "Enabled" check box.
- AVB is still operational but now Tesira IP control is no longer active on the AVB port.
Enable 802.1X
802.1X provides network access control. Tesira server-class devices support 802.1X on the Control, AVB and VoIP ports. If the network is configured with 802.1X, follow the 802.1X article to enable network access control.
Tesira VoIP security
Tesira SVC-2 VoIP interfaces support TLS, SIPS, SRTP and 802.1X. Operation of secured protocols depend on support of the VoIP proxy server. When using Tesira VoIP, follow the VoIP deployment guide for the given VoIP system.
The VoIP interface offers HTTP, HTTPS interfaces for remote configuration and Telnet for debugging. The protocols are disabled by default and may be enabled via the VoIP Control/Status block if required. The Tesira VoIP interface will not operate if VoIP Control/Status blocks are not present in the DSP configuration. Remove VoIP blocks from the Tesira DSP signal flow layout if the VoIP interface will not be used
Analog telephone interface
The analog telephone interface provides audio dialing functionality only. It does not provide any dial-in system access. Remove the TI Control/Status blocks from the Tesira DSP signal flow layout if the telephone interface is not in use.
USB and Bluetooth
TesiraFORTE devices are equipped with a USB audio interface. The USB interface provides audio data only. No file transfer or memory access functionality is provided. Remove USB interface blocks from the Tesira DSP signal flow layout if USB is not in use.
Tesira EX-UBT expander-class devices provide USB audio and Bluetooth audio functionality for laptops and mobile devices. No file transfer or memory access functionality is provided. The Bluetooth name may be customized and discovery may be disabled. It is recommended to set an activity timeout. If USB or Bluetooth is not in use with a EX-UBT device, remove the USB or Bluetooth blocks from the Tesira DSP signal flow layout. See Using the Tesira EX-UBT for further detail.
Biamp SageVue
SageVue is a central monitoring and management platform for Biamp devices. The use of SageVue is not required but is strongly encouraged as it provides additional security enhancements. The host machine running SageVue must have IP connectivity with the Tesira device control ports. See the SageVue configuration - deployment guide for specifics on deploying SageVue.
The following sections assume SageVue is deployed, the Tesira systems configured with the DSP layout, SageVue is able to communicate with Tesira devices on the network, and the logged in user has role permissions to enable the feature. Not all features need to be enabled. SageVue will require the admin credentials of any Tesira system that had system security previously enabled.
SageVue system control
System control locks the Tesira system's admin account to SageVue. The admin account is no longer accessible by any user with Tesira Software. Once a system has been controlled by SageVue, all device maintenance functions, firmware updates and DSP configuration changes are only allowed via SageVue. The admin account credentials are not visible and stored on the SageVue host machine file system. If the access to the SageVue system is lost, the Tesira admin account can only be recovered by factory resetting the Tesira devices.
After system control is enabled, a Tesira user with "Controller" privilege level may be created. The controller privilege level only allows read and write operations on DSP block objects, such as level controls and mixer crosspoints. The controller account is required for Biamp Canvas connection or any third-party control automation system.
Caution: Enabling system control will also password protect the TTP (Tesira Text Protcol) interface used by third-party control automation systems. Any existing control system will be denied access at this point. A controller user must be created and the third-party control programmer must configure this user. Consult with the third-party control programmer before enabling system security.
Enabling System Control
- In the SageVue web interface, navigate to Systems and select the desired system to manage.
- Click the "S" icon on the manage system toolbar. If the "S" icon is not available, unprotect the system first via the lock icon.

- Acknowledge the operation by clicking "Yes, Continue"
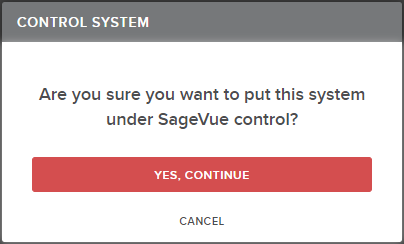
- SageVue now locks the Tesira admin account. The interface will report success when complete. All device management functions must now happen through SageVue. Biamp Canvas control or any third-party control automation system is now locked out at this point. The SageVue system and device views will reflect the "S" icon for devices controlled by SageVue.
- Reload the page to create a controller user. The manage system toolbar will show a plus icon for adding a user.

- Create the control user.
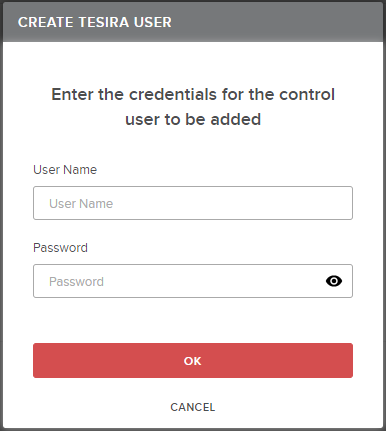
- Provide the controller privilege account to Biamp Canvas users or the third-party control automation system programmer. The controller account cannot send DSP signal flow layout changes. Any DSP configuration changes must be sent from SageVue.
To release control of the Tesira system, navigate back to the manage system page and click the "S" icon again. SageVue will confirm it has released the system and will return Tesira to an unprotected state.
System protection
SageVue system control may not be appropriate for the environment. SageVue may also enable Tesira system security. SageVue will only create the admin user. Any other Tesira user privilege level must be created with Tesira Software. SageVue does not store the admin credentials for each system. Each Tesira system may have unique users and passwords. Any changes to the system via SageVue will require the user to enter the Tesira admin credentials.
A lock icon is displayed on the Systems and Devices views when Tesira system protection is enabled.

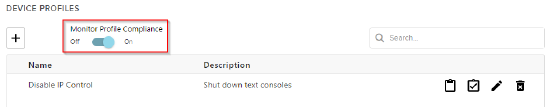
Device Profiles
SageVue device profiles provide a mechanism to mass deploy settings and monitor devices for compliance. Device profiles may be used to monitor that Telnet and SSH are disabled or that 802.1X is enabled. If the device deviates from the profile settings, SageVue will send a device out of compliance alert.
Example of a device profile to disable Telnet and SSH:
- This profile assumes no third-party control systems are connecting via Telnet or SSH.
- Navigate to Device Profiles and click the "+" plus icon to add a new profile.
- Enter a name and description.
- Set the Network tab to active and check the Telnet and SSH properties only.
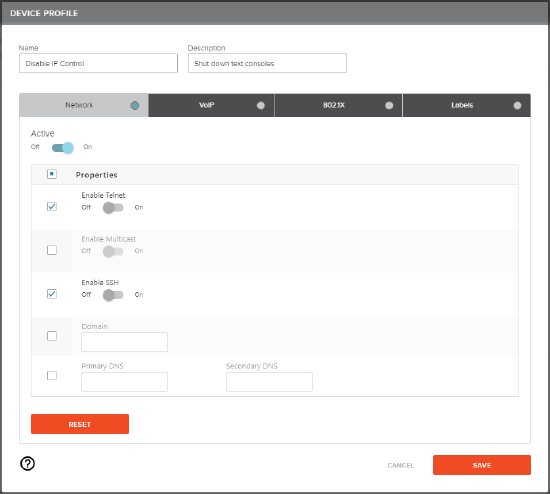
- Save the profile.
- Click the Assign profile button on the profile line.
- Select the Tesira devices to receive the profile and click save.
- Click the Apply profile button to send the profile to the assigned devices.
- Enable Monitor Profile Compliance to receive alerts about out of compliance devices.