Network Security
Securing a networked AV system can help prevent attackers from compromising the network and eavesdropping on audio or video signals. Each network has different needs to address vulnerabilities. This document provides a general overview of network security best practices relating to audio and video networks.
Layered security
It’s best to implement security in a layered approach. If an attacker was able to get through one layer, they would still need to bypass multiple other layers to compromise the system. The security measures taken should address multiple layers of the TCP/IP (Transmission Control Protocol/ Internet Protocol) model instead of focusing all efforts on only one layer. For example, it would be better to have a device behind a locked door (physical), install a firewall (internet), and enable port security (data link) rather than only using a cable lock (physical), have the device behind a locked door (physical), and install security cameras (physical). If a lower layer has vulnerabilities, there is more risk for the upper layers to be compromised. For example, if the data link layer is compromised then all the above layers are compromised as well. Networks are only as secure as the weakest link.
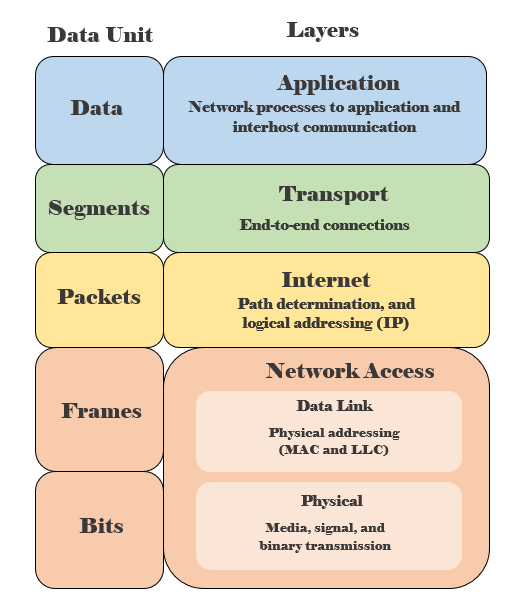
Network security best practices
Network Access Layer
Physical Layer
An intruder could gain access to the network with a computer already on the network or connect their computer to an open network port. If they are able to gain access to the network equipment they could unplug power cords, power off devices, disconnect network cables, connect network cables to different ports, or damage network cables so devices aren't able to communicate.
Locks
Physically control access to equipment rooms with switches, routers, AV equipment, and computers used to communicate with your Biamp devices. It's easier for an unauthorized person to access the system if they use a computer already on the network with the Tesira software already installed. They could also connect directly to the equipments control port to make configuration changes.
Cable management
Cables should be in a secure area so they are unable to be tampered with. Cables connected behind movable podiums can be bent or crimped. Cables that are crimped will result in high packet loss and can cause issues when sending configuration files, updating firmware, and sending audio between devices.
Data Link Layer
An intruder could exploit vulnerabilities in the data link layer to shut down devices, change configuration settings, and gain information on the network for a future attack. Intruders can use a variety of methods within this layer to bring the network down, re-route traffic by connecting a rogue switch or router to a network port, send out poisonous ARP packets, eavesdrop on other conversations, and use network analyzing tools to gather more information on the network for other attack methods.
MAC-based port security
This security method is applied at the switch port level and corresponds to the data link layer for security. Different switch vendors have different methods of applying this type of security, but the general principal is the same for all. The switch can be configured only to allow traffic from one or more specific MAC addresses or the switch can be configured to allow only a certain amount of devices to communicate on that port. This allows only the Tesira device to communicate on the network from this port.
The control port consists of one MAC address and the AVB port can present up to two MAC addresses. The first MAC address on the AVB port is for media and the second MAC address is for control when control functionality is enabled on that port. By default, the AVB port will not be enabled for control traffic and will be only using the first MAC address for AVB traffic.
802.1x
802.1x is a more sophisticated method of securing individual network ports. This method required the end device to present login credentials to the switch once it is connected. The switch will then authenticate the device with a centralized server that will either grant or deny network access to that device. The switch port will not pass any traffic other than packets specific to the 802.1x authentication process. This method is preferred above MAC-based port security for many reasons:
- It authenticates the user in addition to simply authorizing the device.
- It provides a centralized source for user account administration.
- It allows users and devices to move locations and still maintain security without the need to modify switch configurations.
- It provides more flexibility for network administrators to assign specific devices to specific VLANs based on the login credentials provided.
Tesira supports 802.1x on control, AVB, and VoIP ports of any Server class device with release 3.8 and higher in non-server redundant designs.
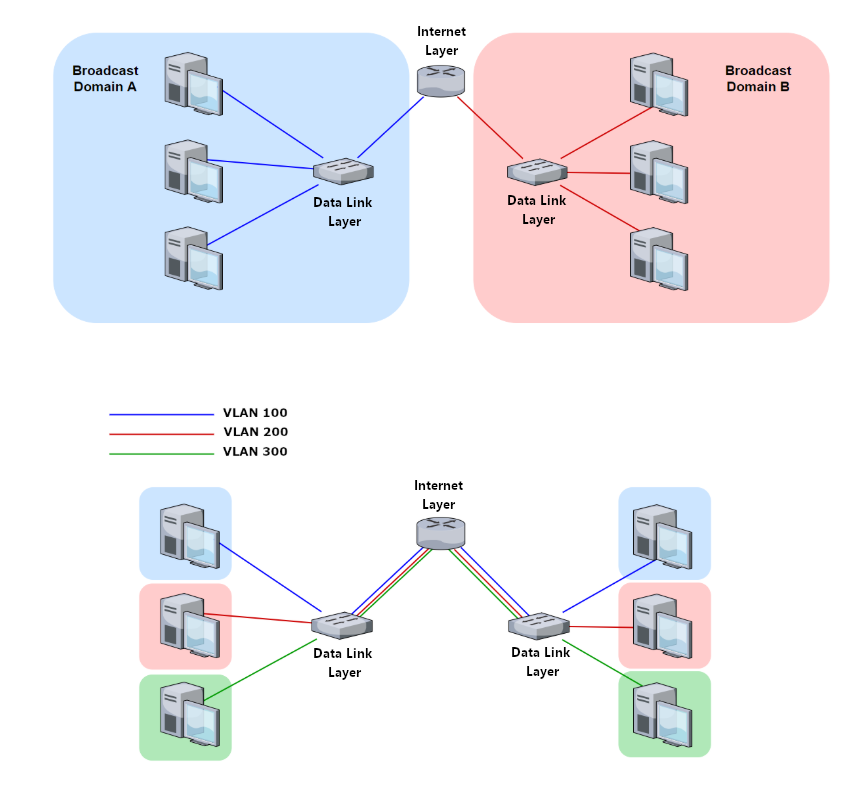
VLANs
Virtual Local Area Networks (VLAN) can be configured on a network switch and help segment networks into broadcast domains. Typically, each VLAN is assigned to its own sub-network but it is possible for devices in the same VLAN to be assigned to different sub-networks. Audio and video devices can be network intensive and isolating AV equipment to it's own physical switch or with VLANs on an existing corporate switch is recommended. Providing a dedicated VLAN for Tesira devices ensures a more stable communication environment. If too much traffic is being sent across the network, other devices will experience slow connections or no connectivity. Breaking up the network with a separate control VLAN and a media VLAN may be beneficial.
It's best practice to configure your own VLANs and not use the default VLANs. Another potential security risk with not having the overall network split up into VLANs is the risk of a DoS attack. If this attack were to happen on one VLAN, the other VLANs would remain intact. Any unconfigured VLAN ports will show traffic being sent across the default VLAN. If an unauthorized person is able to gain access to an un-configured port, they will be able to see all traffic sent across that broadcast domain.
Coordinate with the IT team on the best strategy for setting up VLANs according to their network security policy.
Internet Layer
Any vulnerabilities in the internet layer would provide access to the internal networks across subnets. If this layer is compromised, the intruder would be able to exploit any attacks from the data-link layer and any IP address routing attacks. These would include man-in-the-middle attacks, denial-of-service (DoS) attacks, and packet sniffing.
Selecting an IP address
An important point to remember is never place a Biamp device on the internet with a public IP address. It must always be protected behind a firewall. If a Biamp device has a public IP address, it is much more likely to be subjected to constant attacks and intrusion attempts. Instead, use a private IP address that is not routable across the internet and falls within the ranges:
- 192.168.0.1 - 192.168.255.254
- 172.16.0.1 - 172.31.255.254
- 169.254.0.1-169.254.255.254 (Link-local)
- 10.0.0.1 - 10.255.255.254
Coordinate with the IT team on the best strategy for setting up the IP addressing scheme and network design. Many IT teams have specific addresses set aside for end device assignment. IP addresses should be strategically assigned for scalability on future devices and to ensure there aren't any IP address conflicts.
Firewalls
Security features that should be considered are Dynamic ARP Inspection (DAI) and DHCP (Dynamic Host Control Protocol) snooping. When DHCP snooping is enabled, a table of trusted IP to MAC addresses are created. DAI refers to the DHCP snooping table to block ARP packets with incorrect IP to MAC bindings.
This prevents ARP and MAC spoofing attacks, where the attacker pretends to be a trusted device on the network. This could stop communication between legitimate devices and re-route audio to the attacker.
Transport Layer
Vulnerabilities in the transport layer allow an intruder to eavesdrop on communications, stop communication packets, and access the internal network through an open port. Traffic sent across the network in plain text is susceptible to session hijacking where an intruder changes the destination address of packets.
VoIP port diagnostics
Biamp Voice over IP (VoIP) cards provide password-protected Telnet and HTTP/HTTPS access to diagnostic and configuration information. These features are disabled by default but can be enabled for debugging purposes. However, they will appear as open ports on a network port scan and could violate a network security policy.
By default, Telnet and HTTPS are disabled. Ports that may be used by a Biamp system include:
- 4000-65535 for Real Time Protocol (RTP)
- 23 for Telnet
- 80 for HTTP
- 443 for HTTPS
- 5060 for Session Initiation Protocol (SIP)
- 5061 for Secure SIP (SIPS)
All VoIP ports can be opened or closed to match the network requirements. More information can be found at Tesira network ports and protocols.
Unused ports
Unused ports should be turned off or disabled. Attackers will look for open ports as a way into the network. Some ports need to remain open in order for other Biamp devices to see each other and allow control traffic.
A full list of these ports can be found at Tesira network ports and protocols.
Transport Layer Security (TLS)
Transmitting SIP and RTP using either Transport Control Protocol (TCP) or User Datagram Protocol (UDP) transport methods can present a security risk as neither are encrypted. Biamp VoIP products also support secure Transport Layer Security (TLS) to encrypt all SIP traffic to the proxy server.
Secure RTP (SRTP) can be used to encrypt the RTP audio stream. If the VoIP server supports TLS and SRTP, it can be enabled on some Biamp devices to secure the VoIP traffic. This prevents attackers from listening in on information being sent since the communications are encrypted.
Application Layer
Vulnerabilities in this layer provide access to the network from web server connections, any known vulnerabilities found within the software code, and social engineering attacks. When new firmware is released, vulnerabilities are posted within the release notes and an intruder could exploit known vulnerabilities to gain access to a system.
Passwords
Secure passwords are 8+ characters long that include uppercase and lowercase letters, symbols, and numbers. Don't store passwords in an easily accessible place. For example, don't keep written passwords on sticky notes in your office, a notebook on your desk, or in a word document saved on your computer.
If this security measure is not met, attackers could easily gain access to the internal network by using a brute force or dictionary attack. Unauthorized users could change configurations and disrupt the system.
User access levels
Tesira allows system security to protect certain system configuration and operational features. Each user can be one of five available access levels: Observer, controller, supervisor, designer, administrator. Privilege levels are covered in more detail in Tesira security best practices. A password-protected administrator account is used to manage user privileges and enable/disable system security. When system security is enabled, user login credentials must be provided to access the Tesira Text Protocol (TTP) server. These credentials are required for Telnet and Secure Shell (SSH) access.
User accounts in Biamp Canvas can be used to restrict access to the control surface to specific people. This helps secure the system from unintended programming errors by making sure certain users do not have access to change critical settings. Specific instructions on how to set up, edit, and manage user accounts in Biamp Canvas can be found in our Biamp Canvas Help file Edit User Accounts and our cornerstone article Using Biamp Canvas with multiple Windows user accounts.
Telnet
This is a common remote connection protocol that uses port 23 for connection. Telnet has no authentication or encryption and sends traffic across the network in plain text. As such attackers could use a network analyzer application to look into the network packets. They could gather passwords, confidential information, configuration information, and more.
SSH
Secure Shell (SSH) protocol uses public-key cryptography for authentication and port 22 for connection. SSH will restrict access to the system and prevent attackers from looking into packets sent across the network.
Control port on Tesira server-class devices allows both incoming and outgoing control communication via Telnet or SSH.
- For incoming communication (control from other devices), Tesira hosts a TTP (Tesira Text Protocol) server. Connections to the TTP server can be made using either Telnet or SSH. The TTP server will not provide access to any user information or passwords stored on the system and it is not capable of transmitting or receiving digital audio data.
- For outgoing communication (controlling other devices), a Network Command String block can be added to Tesira configuration. Network Command String block will only send out information that is explicitly included by the programmer in this block's settings.
The ability for Tesira server-class devices to use Telnet and SSH on the Control port can be enabled or disabled via a DEVICE TTP command or in the Device Maintenance Settings > Network Settings dialog. Telnet and SSH are disabled by default. If not required, both Telnet and SSH can remain disabled.
VoIP port on Tesira server-class devices uses Telnet for engineering diagnostics however for installations with security concerns about this port being open, it can be disabled from within the VoIP Property Sheet.
Update firmware
Keeping firmware updated helps eliminate known vulnerabilities. An attacker could easily look at the release notes to exploit known vulnerabilities within the software or firmware. A full list of solved issues can be found at:
The newest firmware and software can be downloaded from:
Unused services
Unused services, features, modules, or applications should be turned off or disabled. Attackers will look for these unused services as a way in and exploit any vulnerabilities they may have.
Monitoring services
Enabling Simple Network Management Protocol (SNMP) allows for monitoring network traffic or device utilization. This can be used for alerts when a spike of unusual activity is occurring and stop potential current attacks. Specifics on using SNMP can be found in Using SNMP with Devio.
SageVue can be used to monitor Tesira and Devio devices for abnormal traffic, DSP usage, creating and modifying user accounts, and pushing firmware updates. More information on all of SageVue's capabilities can be found at SageVue FAQ.
Bluetooth
Bluetooth should be turned off when not in use. If only one device will be consistently paired, connect the devices initially and once device is paired, turn Bluetooth discovery off from the Tesira side. Bluetooth attacks typically scan the area for devices looking to connect via bluetooth and probes for information on known vulnerabilities. This attack doesn't require a paired connection to gather information and can be done when another device is already paired. This can be avoided by turning off bluetooth completely when not in use. Bring your own device networks will need Bluetooth discovery always turned on, unless the room is not in use.
The EX-UBT follows the Bluetooth 4.0 standard. During the pairing process, encryption keys are shared between the two devices and once paired, the Bluetooth connection is fully encrypted.
Other resources
Contact your switch manufacturer on how to implement the configurations mentioned since each manufacturer requires different commands and steps.
Compliance, declaration of origin documents, and other letters can be supplied by emailing support@biamp.com or calling our tech support number at +1 877.242.6796 (877.BIAMP.XO).
Glossary
ARP Poisoning The act of changing a destination MAC address within a packet to a different MAC address used by the attacker.
Brute Force An attack where consecutive guesses are used to access an account or obtain confidential information.
Denial of Service (DoS) An attack that prevents users from accessing the network or a machine by flooding a target with traffic and making it unavailable to any other requests.
Dictionary Attack Automated software that runs through a list of dictionary words to obtain a user's password.
IP Spoofing The act of changing a destination IP address within a packet to a different IP address used by the attacker.
Man-in-the-Middle An attack that allows the intruder to silently eavesdrop on communications or inject malicious code in packets before they reach the destination.
Packet Sniffing Viewing the contents of packets being sent across a network.
Session Hijacking An attack where the intruder takes over an active session by pretending to be the legitimate destination device.
Social Engineering An attack based on human interaction to persuade people into giving up confidential information.
Further reading
- Separated or converged Control and AVB networks
- Tesira security best practices
- AVB streams (IEEE 1722.1)
- Using multiple networked audio protocols
- Tesira network ports and protocols
- Single Network Connection option in Tesira
- External: Understanding Security Using the OSI Model by Glenn Surman
- External: AVIXA RP-C303.01:2018 Recommended Practices For Security In Networked Audiovisual Systems
